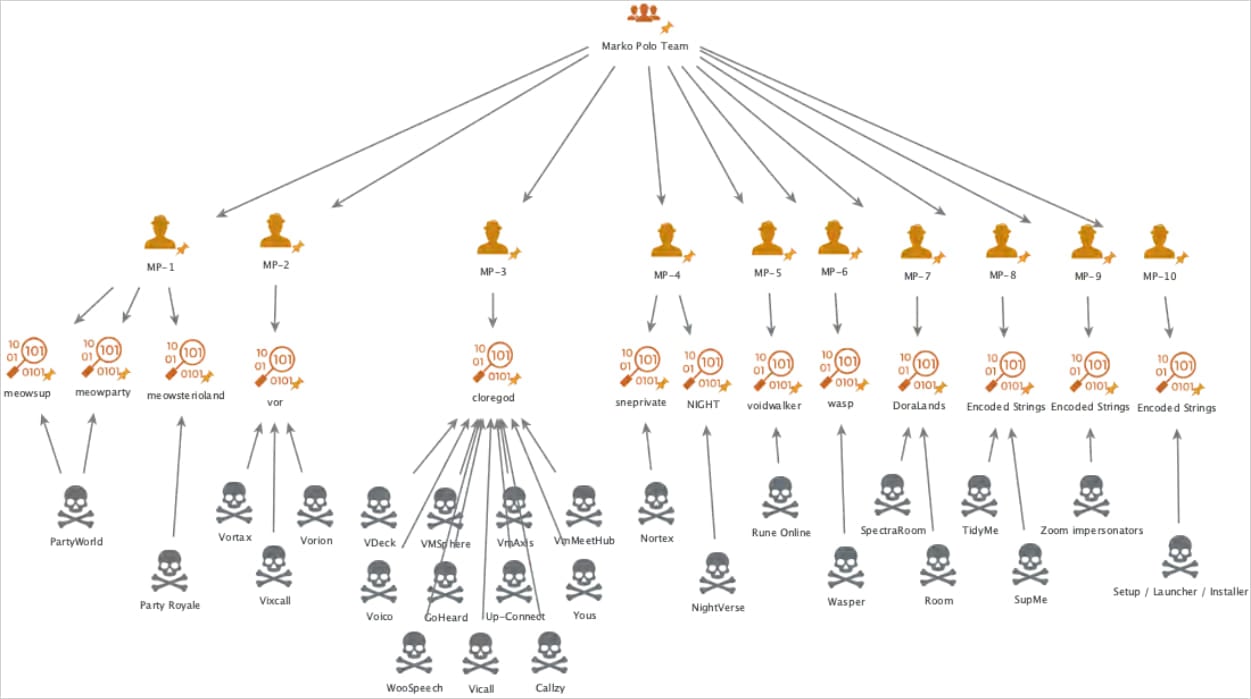
A massive infostealer malware operation encompassing thirty campaigns targeting a broad spectrum of demographics and system platforms has been uncovered, attributed to a cybercriminal group named “Marko Polo.”
The threat actors use a variety of distribution channels, including malvertising, spearphishing, and brand impersonation in online gaming, cryptocurrency, and software, to spread 50 malware payloads, including AMOS, Stealc, and Rhadamanthys.
According to Recorded Future’s Insikt Group, which has been tracking the Marko Polo operation, the malware campaign has impacted thousands, with potential financial losses in the millions.
“Based on the widespread nature of the Marko Polo campaign, Insikt Group suspects that likely tens of thousands of devices have been compromised globally — exposing sensitive personal and corporate data,” warns Recorded Future’s Insikt Group.
“This poses significant risks to both consumer privacy and business continuity. Almost certainly generating millions of dollars in illicit revenue, this operation also highlights the negative economic effects of such cybercriminal activities.”
Source: Recorded Future
Setting high-value traps
Insikt Group reports that Marko Polo primarily relies on spearphishing via direct messages on social media platforms to reach high-value targets such as cryptocurrency influencers, gamers, software developers, and other people likely to handle valuable data or assets.
Victims are lured into downloading malicious software by interacting with what they are tricked into believing are legitimate job opportunities or project collaborations.
Some of the brands that are impersonated include Fortnite (gaming), Party Icon (gaming), RuneScape (gaming), Rise Online World (gaming), Zoom (productivity), and PeerMe (cryptocurrency).
Marko Polo also uses its own made-up brands not related to existing projects, like Vortax/Vorion and VDeck (meeting software), Wasper and PDFUnity (collaboration platforms), SpectraRoom (crypto communications), and NightVerse (web3 game).
In some cases, the victims are led to a website for fake virtual meeting, messaging, and game applications, which are used to install malware. Other campaigns distribute the malware through executables (.exe or .dmg) in torrent files.
Source: Recorded Future
Hitting both Windows and macOS
Marko Polo’s toolkit is diverse, showing the…
Click Here to Read the Full Original Article at BleepingComputer…

