The Chinese state-sponsored hacking group Salt Typhoon has been observed utilizing a new “GhostSpider” backdoor in attacks against telecommunication service providers.
The backdoor was discovered by Trend Micro, which has been monitoring Salt Typhoon’s attacks against critical infrastructure and government organizations worldwide.
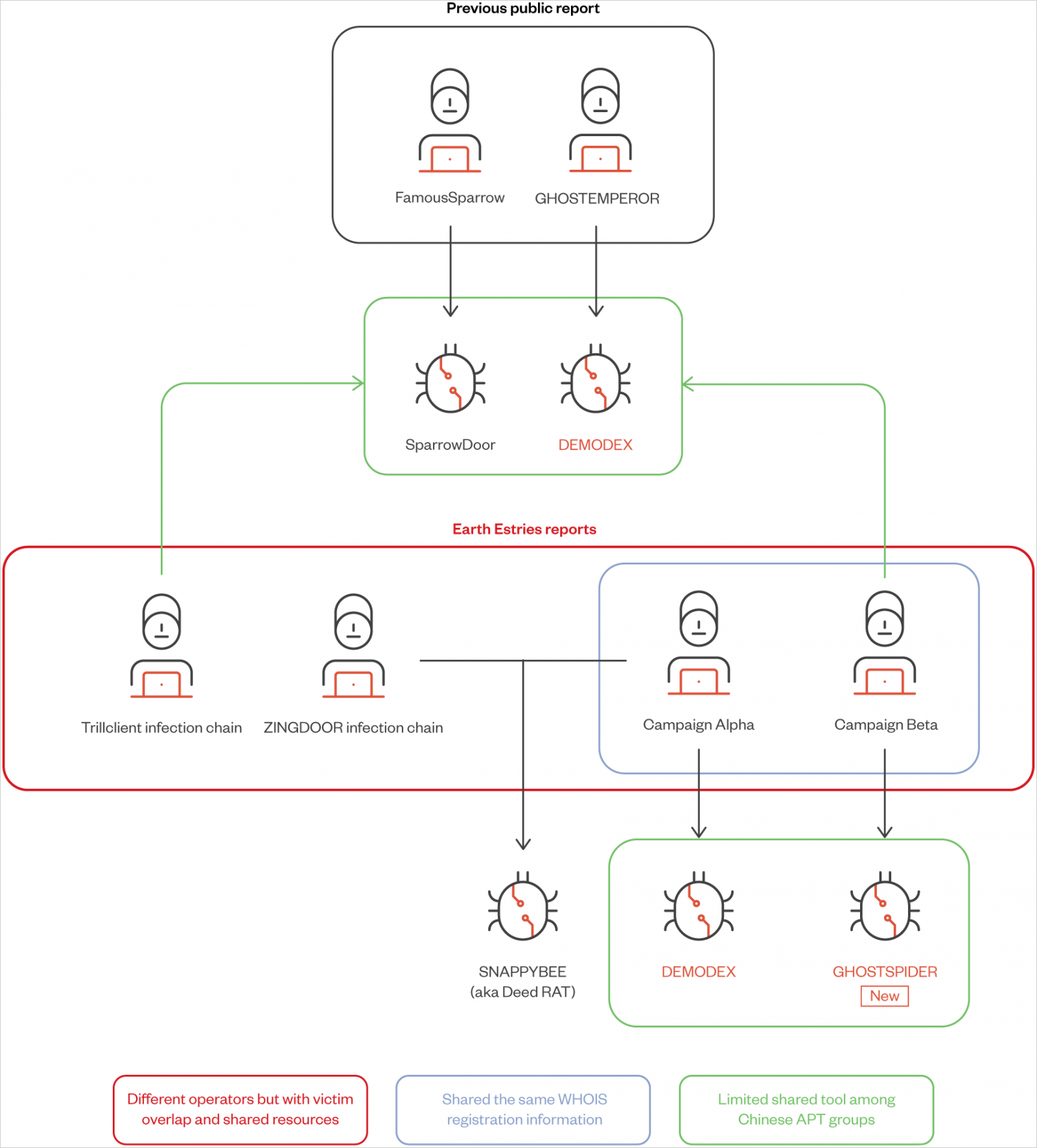
Along with GhostSpider, Trend Micro discovered that the threat group also uses a previously documented Linux backdoor named ‘Masol RAT,’ a rootkit named ‘Demodex,’ and a modular backdoor shared among Chinese APT groups named ‘SnappyBee.’
Source: Trend Micro
Salt Typhoon’s global campaigns
Salt Typhoon (aka ‘Earth Estries’, ‘GhostEmperor’, or ‘UNC2286’) is a sophisticated hacking group that has been active since at least 2019 and typically focuses on breaching government entities and telecommunications companies.
Recently, the U.S. authorities have confirmed that Salt Typhoon was behind several successful breaches of telecommunication service providers in the U.S., including Verizon, AT&T, Lumen Technologies, and T-Mobile.
It was later admitted that Salt Typhoon also managed to tap into the private communications of some U.S. government officials and stole information related to court-authorized wiretapping requests.
Earlier today, the Washington Post reported that the authorities in the U.S. notified 150 victims, mainly in the D.C. area, of the fact that Salt Typhoon had breached the privacy of their communications.
According to Trend Micro, Salt Typhoon has attacked telecommunications, government entities, technology, consulting, chemicals, and transportation sectors in the U.S., Asia-Pacific, Middle East, South Africa, and other regions.
The security researchers have affirmed at least twenty cases of Salt Typhoon successfully compromising critical organizations, including, in some instances, their vendors.
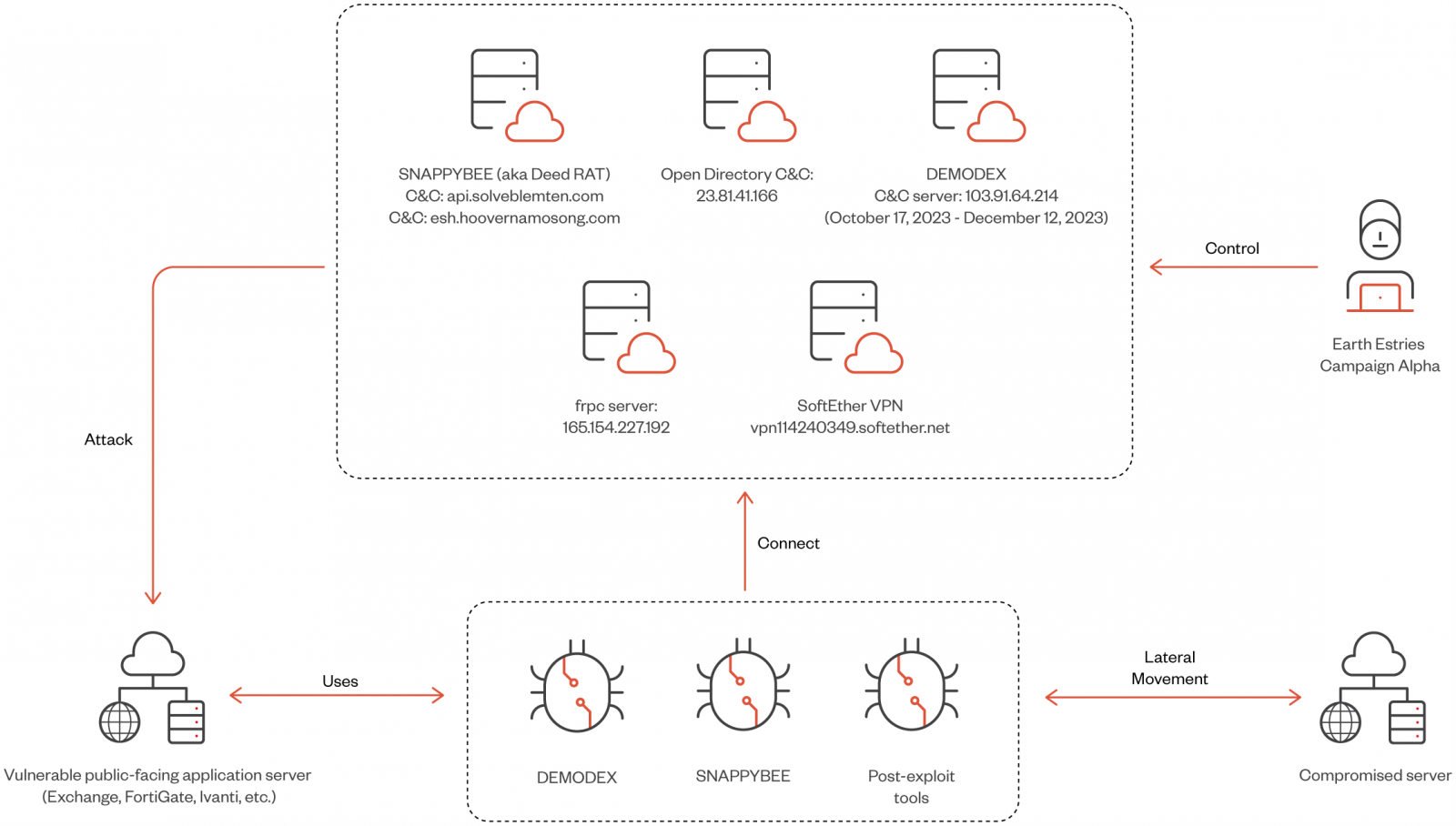
Two campaigns highlighted in the report are ‘Alpha,’ which targeted the Taiwanese government and chemical producers using Demodex and SnappyBee, and ‘Beta,’ a long-term espionage against Southeast Asian telecommunications and government networks, employing GhostSpider and Demodex.
Source: Trend Micro
Initial access is achieved through the exploitation of vulnerable public-facing endpoints, using exploits for the following flaws:
- CVE-2023-46805, CVE-2024-21887 (Ivanti Connect Secure VPN)
- CVE-2023-48788 (Fortinet FortiClient EMS)
- CVE-2022-3236…
Click Here to Read the Full Original Article at BleepingComputer…

