Threat actors are exploiting the massive business disruption from CrowdStrike’s glitchy update on Friday to target companies with data wipers and remote access tools.
As businesses are looking for assistance to fix affected Windows hosts, researchers and government agencies have spotted an increase in phishing emails trying to take advantage of the situation.
Official channel communication
In an update today, CrowdStrike says it “is actively assisting customers” impacted by the recent content update that crashed millions of Windows hosts worldwide.
The company advises customers to verify that they communicate with legitimate representatives through official channels since “adversaries and bad actors will try to exploit events like this.”
“I encourage everyone to remain vigilant and ensure that you’re engaging with official CrowdStrike representatives. Our blog and technical support will continue to be the official channels for the latest updates” – George Kurtz, CrowdStrike CEO
The U.K. National Cyber Security Center (NCSC) also warned that it observed an increase in phishing messages aiming to take advantage of the outage.
Automated malware analysis platform AnyRun noticed “an increase in attempts at impersonating CrowdStrike that can potentially lead to phishing” [1, 2, 3].
Malware cloaked as fixes and updates
On Saturday, cybersecurity researcher g0njxa first reported a malware campaign targeting BBVA bank customers that offered a fake CrowdStrike Hotfix update that installs the Remcos RAT.
The fake hotfix was promoted through a phishing site, portalintranetgrupobbva[.]com, which pretended to be a BBVA Intranet portal.
Enclosed in the malicious archive are instructions telling employees and partners to install the update to avoid errors when connecting to the company’s internal network.
“Mandatory update to avoid connection and synchronization errors to the company’s internal network,” reads the ‘instrucciones.txt’ file in Spanish.
AnyRun, who also tweeted about the same campaign, said that the fake hotfix delivers HijackLoader, which then drops the Remcos remote access tool on the infected system.
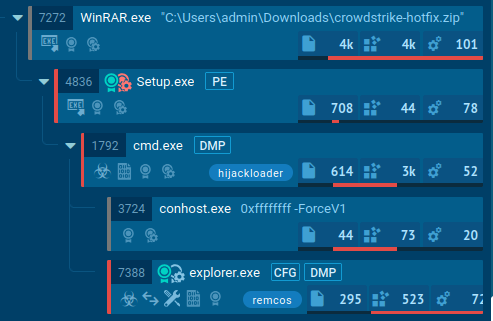
Source: AnyRun
In another warning, AnyRun announced that attackers are distributing a data wiper under the pretense of delivering an update from CrowdStrike.
“It decimates the system by overwriting files with zero bytes and then reports it over #Telegram,” AnyRun says.
This campaign was…
Click Here to Read the Full Original Article at BleepingComputer…

